[ad_1]
Cybersecurity researchers have found a loophole impacting Google Kubernetes Engine (GKE) that might be probably exploited by risk actors with a Google account to take management of a Kubernetes cluster.
The vital shortcoming has been codenamed Sys:All by cloud safety agency Orca. As many as 250,000 energetic GKE clusters within the wild are estimated to be inclined to the assault vector.
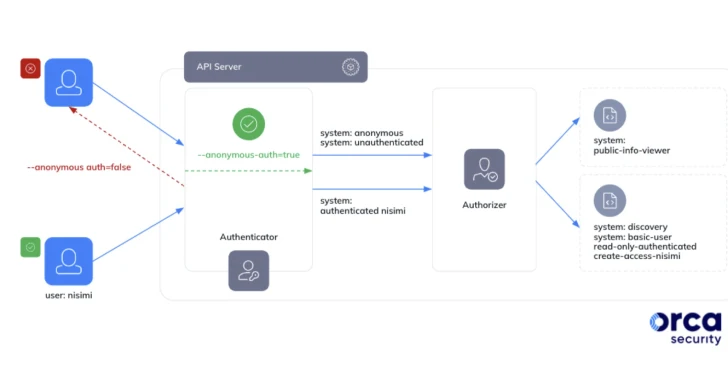
In a report shared with The Hacker Information, safety researcher Ofir Yakobi mentioned it “stems from a possible widespread false impression that the system:authenticated group in Google Kubernetes Engine consists of solely verified and deterministic identities, whereas in truth, it consists of any Google authenticated account (even outdoors the group).”
The system:authenticated group is a particular group that features all authenticated entities, counting human customers and repair accounts. Consequently, this might have critical penalties when directors inadvertently bestow it with overly permissive roles.
Particularly, an exterior risk actor in possession of a Google account might misuse this misconfiguration by utilizing their very own Google OAuth 2.0 bearer token to grab management of the cluster for follow-on exploitation similar to lateral motion, cryptomining, denial-of-service, and delicate information theft.
To make issues worse, this strategy doesn’t depart a path in a fashion that may be linked again to the precise Gmail or Google Workspace account that obtained the OAuth bearer token.
Sys:All has been discovered to impression quite a few organizations, resulting in the publicity of assorted delicate information, similar to JWT tokens, GCP API keys, AWS keys, Google OAuth credentials, non-public keys, and credentials to container registries, the final of which might then be used to trojanize container pictures.
Following accountable disclosure to Google, the corporate has taken steps to dam the binding of the system:authenticated group to the cluster-admin function in GKE variations 1.28 and later.
“To assist safe your clusters in opposition to mass malware assaults that exploit cluster-admin entry misconfigurations, GKE clusters operating model 1.28 and later will not let you bind the cluster-admin ClusterRole to the system:nameless person or to the system:unauthenticated or system:authenticated teams,” Google now notes in its documentation.
Google can also be recommending customers to not bind the system:authenticated group to any RBAC roles, in addition to assess whether or not the clusters have been certain to the group utilizing each ClusterRoleBindings and RoleBindings and take away unsafe bindings.
Orca has additionally warned that whereas there isn’t a public document of a large-scale assault using this methodology, it might be solely a matter of time, necessitating that customers take applicable steps to safe their cluster entry controls.
“Though that is an enchancment, you will need to observe that this nonetheless leaves many different roles and permissions that may be assigned to the group,” the corporate mentioned.
[ad_2]


