
[ad_1]
A brand new publication from Google’s Risk Evaluation Group focuses on business surveillance distributors, whose companies are purchased by governments for monitoring or spying functions. Google is at the moment monitoring greater than 40 CSVs, most of that are extremely technical with the power to develop spyware and adware and zero-day exploits to compromise their targets, notably on Android and iOS units.
Learn particulars about what CSVs goal, how spyware and adware is used, CSVs’ dangerous affect on people and society and the way companies can mitigate these cybersecurity threats.
What are business surveillance distributors, and what do they aim?
Business surveillance distributors are firms that promote full surveillance companies to governmental prospects; these companies embody spyware and adware, infrastructure wanted to speak with the spyware and adware sitting on compromised units. The spyware and adware gives backdoor entry to the units and permits monitoring and information theft.
In line with Google’s Risk Evaluation Group, CSVs function brazenly; that’s, they’ve web sites, advertising content material, gross sales and engineering groups, press relations and typically even attend conferences. Google estimates the variety of CSVs worldwide is inconceivable to rely; additionally, CSVs might change their names a number of instances to keep away from public scrutiny, typically in response to publicity or direct authorized actions towards them.
NSO Group, one of many greatest CSVs and reported since 2015 for its operations, continues to be seen and energetic. That is the case regardless of the corporate being added to the U.S. Entity Listing for malicious cyber actions and authorized actions have been engaged by tech firms, together with Fb and Apple.
What do CSVs goal?
CSV concentrating on is totally different from conventional cyberespionage operations (i.e., superior persistent threats) within the sense that business surveillance distributors goal people, not total networks. This makes the service very useful for somebody who desires to observe or spy on the actions of people, who’re usually dissidents, journalists, human-rights defenders or opposition celebration politicians. Google wrote about such concentrating on beforehand; for instance, in 2022, 5 zero-day vulnerabilities affecting Android customers had been utilized by not less than eight governments and used towards political candidates.
SEE: Prime 8 Superior Risk Safety Instruments and Software program for 2024 (TechRepublic)
Spy ware is the first technique most CSVs use
Spy ware is malicious software program put in on units. Unnoticed by the gadget proprietor, spyware and adware collects customers’ information, sending it again to the controller (i.e., the CSV’s buyer). CSVs typically develop cellular units spyware and adware as a result of their prospects primarily need to gather SMS, messages, emails, places, cellphone calls and even audio/video recordings.
To attain the preliminary compromise of a tool, which is perhaps a pc or a smartphone, spyware and adware generally exploits software program vulnerabilities. This preliminary part may want person interplay, resembling when the spyware and adware makes use of a 1-click exploit, which requires not less than one person interplay, resembling clicking on a hyperlink or opening a file. But much more useful are zero-click exploits, which don’t require any person interplay and could be silently used to drop spyware and adware on the goal’s gadget.
As well as, a number of CSVs present very deep technical experience and have the potential to make use of zero-day vulnerabilities to contaminate units. If the zero-day is found and patched by a vendor, the CSV gives a brand new one to its buyer.
SEE: ESET Risk Report: Android SpinOk SDK Spy ware’s Prevalence and Extra (TechRepublic)
The spyware and adware business’s 4 main classes
- Business surveillance distributors, often known as non-public sector offensive actors, develop and promote the spyware and adware and its infrastructure, together with the preliminary compromise service, the supply of working exploits and information assortment instruments.
- Authorities prospects attain the CSVs to get the service wanted to realize their surveillance objectives. These prospects choose their targets, craft the marketing campaign that delivers the malware, then displays and collects information.
- Particular person vulnerability researchers and exploit builders are the principle sources for CSVs to get working exploits, notably zero-day exploits. A few of these people monetize their abilities legally by working as defenders and serving to enhance software program safety, whereas some others promote the vulnerabilities and/or the associated exploits on to CSVs or exploit brokers. Some CSVs have the interior functionality of doing vulnerability analysis and creating associated exploits.
- Exploit brokers and suppliers are people or firms specialised in promoting exploits. Despite the fact that some CSVs are in a position to develop exploits internally, they typically complement them by buying extra exploits from third events. Google’s researchers notice that brokers can act as intermediaries between sellers, patrons, CSVs and authorities prospects at each step of the method.
Google merchandise are closely focused by CSVs
In line with Google, CSVs are behind half of the identified zero-day exploits concentrating on Google merchandise resembling Chrome and the Android ecosystem, which isn’t stunning, as CSVs largely run spyware and adware concentrating on both Android or iOS cell phones.
From mid-2014 via 2023, 72 zero days used within the wild have been found by the safety researchers; thirty 5 of those 72 exploits have been attributed to CSVs, but it’s a decrease bounds estimate, as there are in all probability exploits not but found and exploits the place attribution stays unknown.
Google’s Risk Evaluation Group has noticed an acceleration within the discovery of zero-day exploits, together with these attributed to CSVs. From 2019 to 2023, 53 zero-day exploits had been found, and 33 of them had been attributed to CSVs.
CSVs can price a number of million USD
The worth tags for CSVs’ companies could be within the tens of millions. For example, in 2022, Amnesty Worldwide uncovered a leaked business proposal from CSV Intellexa originating from the XSS.is cybercrime discussion board. The proposal offered the complete CSV service for a 12 months, with Android and iOS assist, 10 simultaneous contaminated units and extra, for $8 million EUR (Determine A).
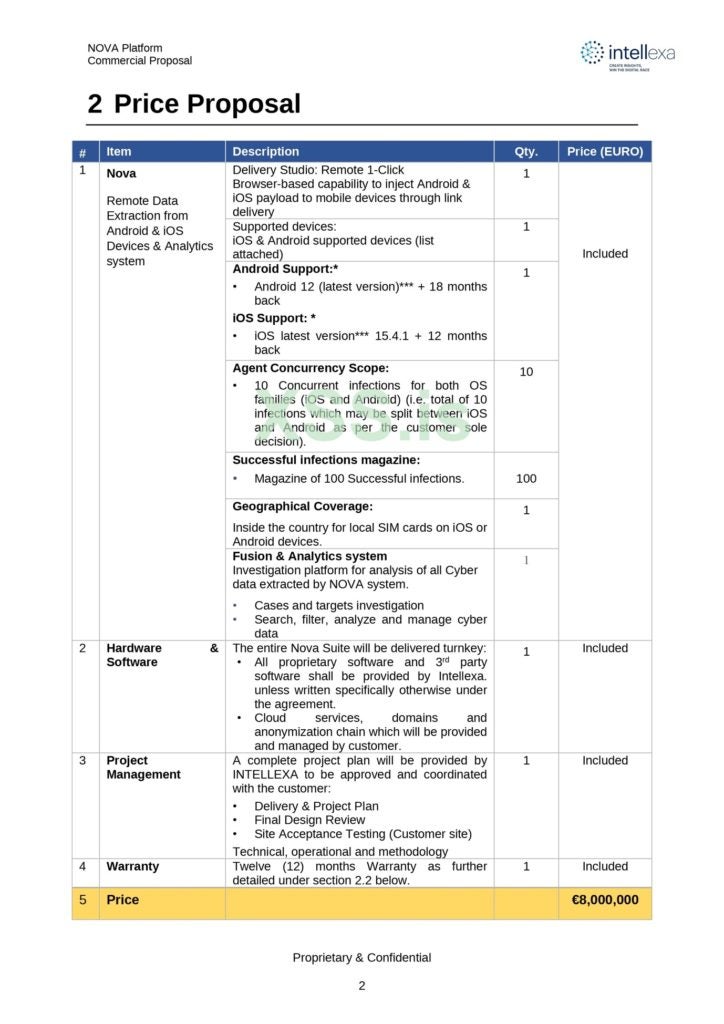
Extra CSV companies could be purchased. Within the case of the Predator spyware and adware, for instance, including persistence prices €3 million EUR greater than the principle provide. Persistence permits the shopper to have the spyware and adware keep on the cellphone even whether it is shut down and restarted.
Reported and potential hurt brought on by CSVs
Conventional cyberespionage operations usually steal information from networks or computer systems, however much less typically from cell phones, in opposition to spyware and adware.
Listed below are two examples from the Google report of hurt brought on by CSVs:
Maria Luisa Aguilar Rodriguez, a world advocacy officer, and Santiago Aguirre, director of the Mexico metropolis based mostly human rights group Centro PRODH, do not forget that falling for such an assault was “terrifying,” as each had been focused by a CSV buyer. Aguirre heard his personal voice within the native information on the radio, as if he had been in league with the native cartels. All of the audio had been stolen from his cell phone and closely edited from totally different calls.
Galina Timchenko, co-founder and chief govt officer of the exiled Russian media outlet Meduza, was focused by a CSV round February 2023. She wrote that “for weeks they’d full entry to my correspondence, so they might see my shut circle. I used to be afraid for them. I used to be afraid for my buddies, my colleagues and Meduza’s companions.” Then she realized a number of of the reporters who’ve been hacked with the Pegasus spyware and adware have been killed, including concern for her personal security along with her buddies and contacts.
As well as, the usage of spyware and adware may additionally have an effect on society at giant. When concentrating on political candidates, “it threatens a society’s capacity to carry free and honest elections,” wrote Google’s Risk Evaluation Group.
How vulnerability researchers shield towards CSVs
Actors within the vulnerability analysis subject assist shield towards CSVs by reporting vulnerabilities to software program distributors in order that zero-day vulnerabilities get patched, but the time of response from the preliminary report back to the discharge of the patch may take weeks or months. Each time a zero-day vulnerability is patched, it not solely protects customers and corporations, however it additionally prevents CSVs from assembly their agreements with prospects and prevents them from being paid, along with rising their operations’ prices.
How companies can mitigate this spyware and adware risk
Listed below are the steps firms ought to take to scale back the chance of this safety risk:
- Implement cellular safety options on all staff’ cellular units.
- Prepare staff to detect compromise makes an attempt on their cell phones, particularly within the case of 1-click exploits, which require the person to click on on a hyperlink or open a file. Suspicious information should solely be opened in sandboxes or in environments operating full host and community safety options.
- Deploy safety patches for cellular working methods and cellular software program as quickly as attainable to keep away from being compromised by zero-click exploits.
- Don’t retailer delicate information on cell phones, if attainable.
- Flip cell phones off throughout delicate conferences to keep away from conversations being intercepted by a compromised gadget.
Editor’s notice: TechRepublic contacted Google for added details about this spyware and adware analysis. If we obtain these particulars, this text might be up to date with that data.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.
[ad_2]