
[ad_1]
E mail assaults counting on QR codes surged within the final quarter, with attackers particularly focusing on company executives and managers, reinforcing suggestions that corporations place extra digital protections round their enterprise management.
Making issues worse, phishing emails utilizing QR codes (aka “quishing”) can usually get by spam filters, with assaults focusing on customers of Microsoft 365 and DocuSign efficiently touchdown in e mail inboxes, in accordance with a report printed this week by Irregular Safety, a supplier of cloud e mail safety.
Within the fourth quarter of 2023, the typical high govt within the C-suite noticed 42 instances extra phishing assaults utilizing QR codes in comparison with the typical worker. Different managerial roles suffered a rise in assaults as properly, though considerably smaller, with these non-C-suite executives encountering 5 instances extra QR-code-based phishing assaults, in accordance with the corporate’s report.
General, the information demonstrates that attackers have executives — and different privileged customers — of their websites, says Mike Britton, CISO for Irregular Safety.
“If I am an attacker, I wish to assault the those that have the power for me to receives a commission and have credentials that give me entry to probably the most fascinating info,” he says. “Or I wish to faux to be these folks, as a result of as soon as once more, social engineering requires that belief, [for a victim to think,] hey, this VP of gross sales or this VP of HR is asking me to do one thing, [making them] sometimes extra probably … to take motion.”
Whereas QR codes have been round for 3 many years, they grew to become rather more fashionable throughout the pandemic, as eating places and different companies directed prospects to contact-free and on-line ordering. In a enterprise context, a high use case for QR codes is providing hyperlinks to ease the sign-up course of for multifactor authentication (MFA). Cyberattackers have hopped on: Greater than 1 / 4 of QR code assaults (27%) in This autumn have been faux notices of MFA, for instance, whereas about one-in-five assaults (21%) have been faux notifications a few shared doc, in accordance with Irregular Safety’s report.
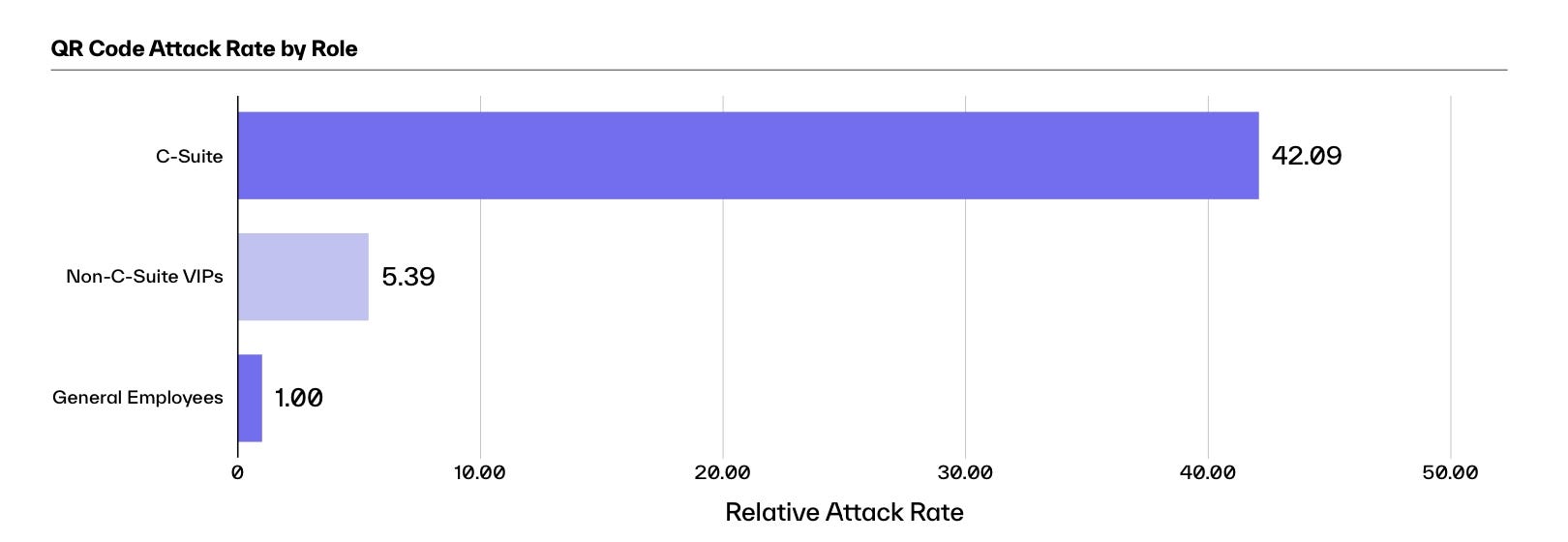
Prime executives see 42 instances extra assaults utilizing QR codes than common staff. Supply: Irregular Safety
As a result of attackers cover their phishing hyperlink in a picture, QR code phishing bypasses consumer suspicions and a few e mail safety merchandise. As well as, malicious QR codes will be positioned in bodily areas utilizing a easy sticker, bypassing digital safety altogether.
“Assaults exploit customers’ inherent belief in QR codes, embedding them in on a regular basis objects like parking meters or posters,” says Monique Becenti, director of product at mobile-security agency Zimperium. “The success price of phishing with QR codes will surpass conventional phishing strategies as a result of they usually bypass customers’ typical suspicion triggers, similar to typos within the URL, resulting in the next probability of scanning them.”
But One other Method to Steal Exec’s Credentials
For probably the most half, quishing attackers who give attention to executives are after the credentials — usernames and passwords — of privileged customers. Credential phishing is the most well-liked type of e mail assault, accounting for 73% of all assaults by the vector and 84% of assaults utilizing a QR code; they usually usually result in extra important compromises, says Irregular Safety’s Britton.
“The first objective is getting at a consumer to steal their credentials,” he says. “As soon as I’ve your credentials, I can do much more harm, and I can do numerous lasting harm. If I’ve your credentials, I can log into your account, I can see who you’ve got despatched emails to, I can ship emails pretending to be you, and I can create mail filter guidelines.”
That final level is a standard technique to abuse mail credentials, Britton says. The attacker will create a blind carbon copy (BCC) rule that forwards all emails to the attacker’s account.
Additional, “menace actors additionally acknowledge that always a number of folks have entry to an govt’s inbox, similar to govt assistants,” the report acknowledged. “Consequently, each particular person who is aware of the login credentials for a VIP’s inbox represents a possible entry level that may be exploited by an attacker.”
Thwarting Quishing Takes Expertise & Coaching the Human
The excellent news is, since October, QR-code phishing has subsided to a big diploma, after accounting for 22% of phishing assaults, in accordance with human-risk administration agency Hoxhunt. “Since final October, we have seen proof that e mail filters are catching as much as the QR phishing method,” says Jon Gellin, menace crew lead at Hoxhunt. “As fewer of those assaults are bypassing e mail filters, there’s been a resultant lower of their recognition.”
Nevertheless, even when quishing subsides, it is going to stay a software for attackers, a lot in the best way that shortened URLs and picture spam proceed for use in cyberattacks. The easiest way to guard customers is to coach them, Gellin says. About 5% of customers reply to a phishing assault inside the first jiffy, suggesting {that a} well-trained pool of staff will help blunt an assault.
“Because the QR phishing pattern has proven, some threats will at all times slip previous even probably the most refined filters,” he says. “At that time, it is as much as the human layer to have the talents and instruments to take care of the menace successfully.”
Coaching is essential, however as a result of a single failure can have a big affect, technical controls are vital, says Irregular Safety’s Britton.
“There, there are some phishing assaults that I’ve seen that even I’ve to get a second opinion from folks as a result of they appear so actual,” he says. “How do I anticipate an HR particular person to get that proper each time? How do I anticipate an accounts payable particular person? How do I anticipate a monetary analyst?”
“Coaching is essential, however we will fail, and it solely takes one failure,” he says.
[ad_2]