[ad_1]
A risk actor generally known as Prolific Puma has been sustaining a low profile and working an underground hyperlink shortening service that is provided to different risk actors for at the least over the previous 4 years.
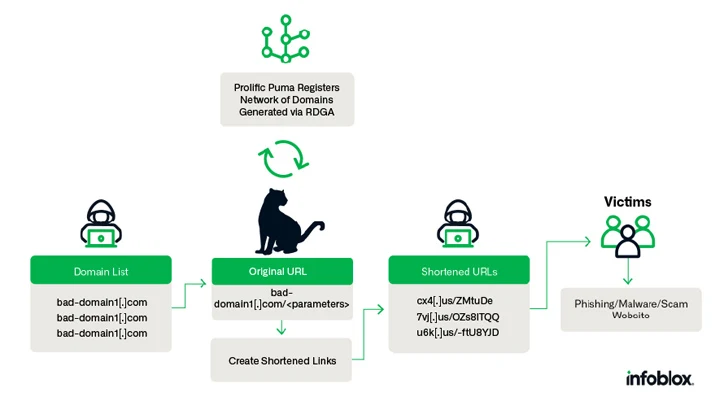
Prolific Puma creates “domains with an RDGA [registered domain generation algorithm] and use these domains to offer a hyperlink shortening service to different malicious actors, serving to them evade detection whereas they distribute phishing, scams, and malware,” Infoblox mentioned in a brand new evaluation pieced collectively from Area Title System (DNS) analytics.
With malicious actors recognized to make use of hyperlink shorteners for phishing assaults, the adversary performs an necessary position within the cybercrime provide chain, registering between 35,000 to 75,000 distinctive domains since April 2022. Prolific Puma can also be a DNS risk actor for leveraging DNS infrastructure for nefarious functions.
A notable side of the risk actor’s operations is the usage of an American area registrar and webhosting firm named NameSilo for registration and title servers attributable to its affordability and an API that facilitates bulk registration.
Prolific Puma, which doesn’t promote its shortening service on underground markets, has additionally been noticed resorting to strategic ageing to park registered domains for a number of weeks previous to internet hosting their service with nameless suppliers.
“Prolific Puma domains are alphanumeric, pseudo-random, with variable size, usually 3 or 4 characters lengthy, however we’ve got additionally noticed SLD labels so long as 7 characters,” Infoblox defined.
Moreover, the risk actor has registered 1000’s of domains within the U.S. top-level area (usTLD) since Might 2023, repeatedly utilizing an e mail handle containing a reference to the music OCT 33 by a psychedelic soul band known as Black Pumas: blackpumaoct33@ukr[.]internet.
The actual-world id and origins of Prolific Puma stays unknown as but. That mentioned, a number of risk actors are mentioned to be utilizing the providing to take guests to phishing and rip-off websites, CAPTCHA challenges, and even different shortened hyperlinks created by a distinct service.
In a single occasion of a phishing-cum-malware assault documented by Infoblox, victims clicking on a shortened hyperlink are taken to a touchdown web page that requests them to offer private particulars and make a fee, and in the end infect their methods with browser plugin malware.
The disclosure comes weeks after the corporate uncovered one other persistent DNS risk actor codenamed Open Tangle that leverages a big infrastructure of lookalike domains of legit monetary establishments to focus on shoppers for phishing and smishing assaults.
“Prolific Puma demonstrates how the DNS may be abused to assist prison exercise and stay undetected for years,” it mentioned.
Kopeechka Hacking Software Floods On-line Platforms with Bogus Accounts
The event additionally follows a brand new report from Development Micro, which discovered that lesser-skilled cybercriminals are utilizing a brand new instrument known as Kopeechka (which means “penny” in Russian) to automate the creation of a whole lot of pretend social media accounts in only a few seconds.
“The service has been lively because the starting of 2019 and supplies straightforward account registering companies for common social media platforms, together with Instagram, Telegram, Fb, and X (previously Twitter),” safety researcher Cedric Pernet mentioned.
Kopeechka supplies two kinds of totally different e mail addresses to assist with the mass-registration course of: e mail addresses hosted in 39 domains owned by the risk actor and people which might be hosted on extra common e mail internet hosting companies similar to Gmail, Hotmail, Outlook, Rambler, and Zoho Mail.
“Kopeechka doesn’t truly present entry to the precise mailboxes,” Pernet defined. “When customers request for mailboxes to create social media accounts, they solely get the e-mail handle reference and the particular e mail that incorporates the affirmation code or URL.”
It is suspected that these e mail addresses are both compromised or created by the Kopeechka actors themselves.
With on-line companies incorporating cellphone quantity verification to finish registration, Kopeechka allows its prospects to select from 16 totally different on-line SMS companies, most of which originate from Russia.
Apart from accelerating cybercrime and equipping risk actors to launch full-fledged operations at scale, such instruments – created as a part of the “as-a-service” enterprise mannequin – spotlight the professionalization of the prison ecosystem.
“Kopeechka’s companies can facilitate a simple and inexpensive strategy to mass-create accounts on-line, which could possibly be useful to cybercriminals,” Pernet mentioned.
“Whereas Kopeechka is especially used for a number of accounts creation, it may also be utilized by cybercriminals who wish to add a level of anonymity to their actions, as they don’t want to make use of any of their very own e mail addresses to create accounts on social media platforms.”
[ad_2]