[ad_1]
A brand new Rust-based macOS malware spreading as a Visible Studio replace to supply backdoor entry to compromised methods makes use of infrastructure linked to the notorious ALPHV/BlackCat ransomware gang.
The marketing campaign delivering the backdoor began since a minimum of November 2023 and remains to be underway distributing newer variants of the malware.
Written in Rust, the malware can run on Intel-based (x86_64) and ARM (Apple Silicon) architectures, say researchers at cybersecurity firm Bitdefender, who’re monitoring it as RustDoor.
Potential hyperlink to ransomware operations
Whereas analyzing RustDoor, malware researchers at Bitdefender found that the malware communicated with 4 command and management (C2) servers.
Taking a look at menace intelligence knowledge, the analysts discovered that three of them had been utilized in assaults doubtlessly linked to ransomware assaults from an ALPHV/BlackCat affiliate.
Nevertheless, the researchers spotlight that that is inadequate proof to confidently hyperlink using RustDoor to a specific menace actor and that “artifacts and IoCs [indicators of compromise] recommend a doable relationship with the BlackBasta and ALPHV/BlackCat ransomware operators.”
With cybercriminals having much less freedom in selecting their infrastructure and being restricted to internet hosting providers that present anonymity and condone criminal activity, it is not uncommon for a number of menace actors to make use of the identical servers for assaults.
Whereas encryptors for the macOS system exist, builds for Apple M1 from LockBit created earlier than December 2022, there are not any public reviews right now of ransomware attacking Apple’s working system.
Most operations goal Home windows and Linux methods as enterprise environments use servers operating these working methods.
Distribution particulars
RustDoor is distributed primarily as an updater for Visible Studio for Mac, Microsoft’s built-in improvement surroundings (IDE) for the macOS platform, which will probably be discontinued this 12 months on August 31.
The macOS backdoor is delivered underneath a number of names, together with ‘zshrc2,’ ‘Previewers,’ ‘VisualStudioUpdater,’ ‘VisualStudioUpdater_Patch,’ ‘VisualStudioUpdating,’ ‘visualstudioupdate,’ and ‘DO_NOT_RUN_ChromeUpdates‘.
Based on Bitdefender, the malware has been underneath energetic distribution and have been undetected for a minimum of three months.
The researchers found three variations of the malware, which come as FAT binaries that embody Mach-O information for each x86_64 Intel and ARM architectures however don’t come bundled in typical dad or mum information comparable to Utility Bundles or Disk Picture.
Bitdefender says this atypical distribution technique reduces the marketing campaign’s digital footprint and the probability of safety merchandise flagging the backdoor as suspicious.
Backdoor capabilities
In a report this week, the researchers say that RustDoor has instructions to regulate the compromised system and to exfiltrate knowledge, and it may persist on the system by modifying system information.
After infecting a system, the malware communicates with command and management (C2) servers utilizing particular endpoints for registration, process execution, and knowledge exfiltration.
The instructions supported by the malware embody the next:
- ps: Lists operating processes, helpful for monitoring system exercise.
- shell: Executes arbitrary shell instructions, giving attackers direct management.
- cd: Adjustments the present listing, permitting navigation by the file system.
- mkdir: Creates a brand new listing, helpful for organizing stolen knowledge or malware elements.
- rm: Removes information, doubtlessly for deleting essential information or cleansing up traces of the malware.
- rmdir: Removes directories, just like rm however for directories.
- sleep: Pauses execution for a set time, presumably to evade detection or synchronize actions.
- add: Sends information to a distant server, used for exfiltrating stolen knowledge.
- botkill: Terminates different malware processes, presumably to remove competitors or free system assets.
- dialog: Shows messages or prompts to the consumer, doubtlessly for phishing or to execute instructions with consumer privileges.
- taskkill: Ends specified processes, helpful for stopping safety software program or different processes interfering with malware.
- obtain: Retrieves information from a distant server, used for bringing extra malware elements or updates onto the contaminated system.
The backdoor makes use of Cron jobs and LaunchAgents to schedule its execution at particular instances or when the consumer logs in, thus ensuring it survives system reboots.
Furthermore, it modifies the ~/.zshrc file to execute in new terminal classes or add it to the Dock with system instructions, which helps it mix in with official functions and consumer actions.
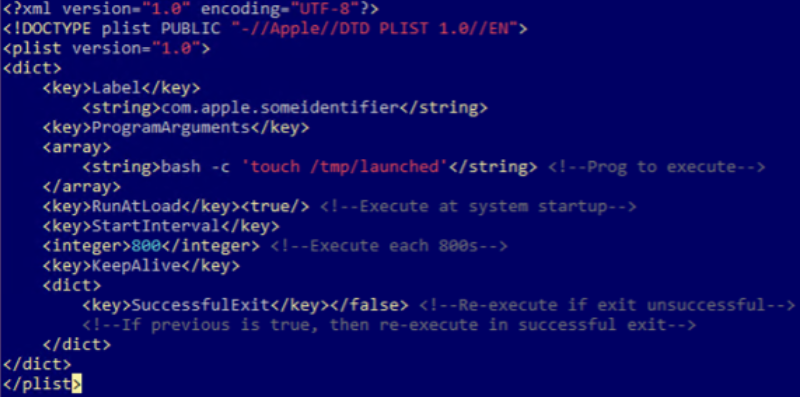
Bitdefender notes that there are a minimum of three variants of RustDoor, the earliest one seen since early October 2023.
The following one was seen November 22 and seemed to be a testing model that preceded an up to date model noticed on November 30, which incorporates “a fancy JSON configuration in addition to an embedded Apple script used for exfiltration” of information with particular extensions.
The researchers present an inventory of identified indicators of compromise for RustDoor, which incorporates binaries, obtain domains, and URLs for the 4 command and management servers found.
[ad_2]