[ad_1]
A menace actor affiliated with Iran’s Ministry of Intelligence and Safety (MOIS) has been noticed waging a complicated cyber espionage marketing campaign concentrating on monetary, authorities, army, and telecommunications sectors within the Center East for at the least a yr.
Israeli cybersecurity agency Examine Level, which found the marketing campaign alongside Sygnia, is monitoring the actor underneath the title Scarred Manticore, which is alleged to intently overlap with an rising cluster dubbed Storm-0861, one of many 4 Iranian teams linked to harmful assaults on the Albanian authorities final yr.
Victims of the operation span numerous international locations similar to Saudi Arabia, the United Arab Emirates, Jordan, Kuwait, Oman, Iraq, and Israel.
Scarred Manticore additionally displays some extent of overlap with OilRig, one other Iranian nation-state crew that was just lately attributed to an assault on an unnamed Center East authorities between February and September 2023 as a part of an eight-month-long marketing campaign.
One other set of tactical overlaps have been found between the adversary and an intrusion set codenamed ShroudedSnooper by Cisco Talos. Assault chains orchestrated by the menace actor have singled out telecom suppliers within the Center East utilizing a stealthy backdoor generally known as HTTPSnoop.
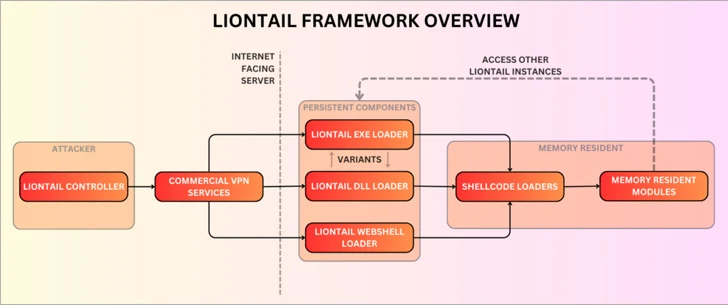
The exercise represented by Scarred Manticore is characterised by means of a beforehand unknown passive malware framework known as LIONTAIL that is put in on Home windows servers. The menace actor is believed to be energetic since at the least 2019.
“Scarred Manticore has been pursuing high-value targets for years, using a wide range of IIS-based backdoors to assault Home windows servers,” Examine Level researchers stated in a Tuesday evaluation. “These embrace a wide range of customized net shells, customized DLL backdoors, and driver-based implants.”
A complicated piece of malware, LIONTAIL is a group of customized shellcode loaders and reminiscence resident shellcode payloads. A noteworthy part of the framework is a lightweight-yet-sophisticated implant written in C that permits attackers to execute instructions remotely by way of HTTP requests.
The assault sequences entail infiltrating publicly dealing with Home windows servers to kick off the malware supply course of and systematically harvest delicate information from contaminated hosts.
“As a substitute of utilizing the HTTP API, the malware makes use of IOCTLs to work together immediately with the underlying HTTP.sys driver,” the researchers stated, detailing the command-and-control (C2) mechanism.
“This strategy is stealthier because it would not contain IIS or HTTP API, that are normally intently monitored by safety options, however shouldn’t be a simple job on condition that the IOCTLs for HTTP.sys are undocumented and require further analysis efforts by the menace actors.”
From a technical standpoint, one intriguing aspect of the operation is that the menace actor employs a tailored implant for every compromised server, permitting the malicious actions to mix into the sufferer atmosphere and make it arduous to differentiate between suspicious and bonafide community site visitors.
Additionally deployed alongside LIONTAIL embrace numerous net shells and an online forwarder instrument known as LIONHEAD, an online forwarder.
Historic exercise of Scarred Manticore signifies a steady evolution of the group’s malware arsenal, what with the menace actor beforehand counting on net shells similar to Tunna and a bespoke model known as FOXSHELL for backdoor entry.
Since mid-2020, the menace actor can also be stated to have used a .NET-based passive backdoor known as SDD that establishes C2 communication by means of an HTTP listener on the contaminated machine with the final word objective of executing arbitrary instructions, importing and downloading recordsdata, and operating further .NET assemblies.
The progressive updates to the menace actor’s ways and instruments is typical of superior persistent menace (APT) teams and demonstrates their sources and diverse expertise. That is finest exemplified by Scarred Manticore’s use of a malicious kernel driver known as WINTAPIX that was uncovered by Fortinet earlier this Could.
In a nutshell, WinTapix.sys acts as a loader to execute the following stage of the assault, injecting an embedded shellcode into an acceptable consumer mode course of that, in flip, executes an encrypted .NET payload particularly designed to focus on Microsoft Web Info Companies (IIS) servers.
The concentrating on of Israel comes amid the ongoing Israel-Hamas struggle, prompting low-sophistication hacktivist teams to assault numerous organizations within the nation, in addition to nations like India and Kenya, suggesting nation-state actors’ reliance on info operations geared toward influencing the worldwide notion of the battle.
The U.S. Federal Bureau of Investigation (FBI), in an announcement to the Senate Committee on Homeland Safety and Governmental Affairs (HSGAC) earlier this week, warned that the state of affairs has the potential to worsen the “cyber concentrating on of American pursuits and demanding infrastructure” by Iran and non-state actors alike.
“LIONTAIL framework elements share comparable obfuscation and string artifacts with FOXSHELL, SDD backdoor, and WINTAPIX drivers,” Examine Level stated.
“Analyzing the historical past of their actions, it turns into evident how far the menace actor has are available bettering their assaults and enhancing their strategy which depends on passive implants.”
[ad_2]