[ad_1]
The browser has change into the primary work interface in trendy enterprises. It is the place staff create and work together with information, and the way they entry organizational and exterior SaaS and net apps. Because of this, the browser is extensively focused by adversaries. They search to steal the information it shops and use it for malicious entry to organizational SaaS apps or the internet hosting machine. Moreover, unintentional information leakage by way of the browser has change into a essential concern for organizations as effectively.
Nevertheless, conventional endpoint, community, and information safety options fail to guard this essential useful resource towards superior web-borne assaults that repeatedly rise in sophistication and quantity. This hole leaves organizations uncovered to phishing assaults, malicious browser extensions, information publicity, and information loss.
That is the problem LayerX is trying to resolve. LayerX has developed a safe enterprise browser extension that may be mounted on any browser. The LayerX extension delivers complete visibility, steady monitoring, and granular coverage enforcement on each occasion throughout the looking session. Utilizing proprietary Deep Session Evaluation expertise, LayerX can mitigate browser information loss dangers, forestall credential theft by phishing websites, establish malicious extensions, and rather more.
On this platform evaluate, we’ll stroll you thru your complete LayerX person journey, from preliminary set up and configuration to visibility and safety. (to get a customized demo of Layerx, go to their web site right here)
Preliminary Set up and Setup
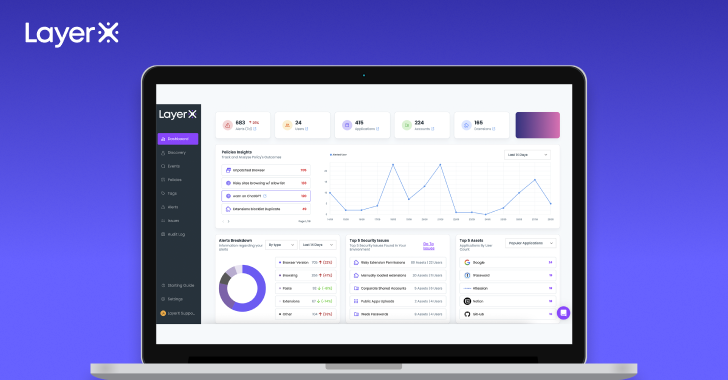
LayerX is designed for straightforward set up on prime of the group’s present browser infrastructure. The person can distribute it by way of a bunch coverage, any enterprise system administration platform, or the browser’s administration workspace. For the final possibility, LayerX just isn’t put in on the internet hosting system. As an alternative, it’s delivered as a part of the browser’s profile, making it a pure alternative for the safety of unmanaged gadgets. The set up display enabled the person to decide on the browsers which can be in use of their setting.
 |
| Determine 1: The LayerX set up display. Centralized distribution (left), browser administration sign-in (proper) |
The LayerX Dashboard
As soon as the set up is full, the LayerX dashboard instantly turns into populated with pre-defined insurance policies, info on the browsers, customers, extensions, and net exercise. When the person configures insurance policies, the dashboard will present them as effectively, together with their standing, detected danger alerts, and different information aggregations.
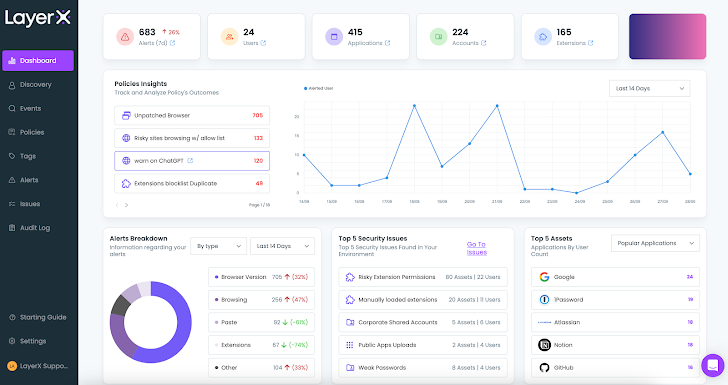 |
| Determine 2: LayerX dashboard |
The dashboard supplies high-level insights into the safety posture of the browser ecosystem. For drilling down into particular points, let’s transfer on to the Discovery web page.
Visibility and Discovery of Entities in Shopping Classes
The Discovery web page supplies the person with a wealth of details about 5 sorts of entities:
- Customers
- Apps
- Accounts
- Extensions
- Browsers
For instance:
- The ‘Apps’ part exhibits customers all the net and SaaS purposes the group’s staff are accessing by way of their browsers. This contains 100% of the apps in use, no matter whether or not they’re sanctioned or private.
- The ‘Accounts’ part exhibits the energy of the account’s passwords or any utilization of non-corporate identities. The person can also uncover browsers which can be operating outdated variations, implement updates, and achieve visibility into all of the completely different extensions which can be put in on browsers within the ecosystem.
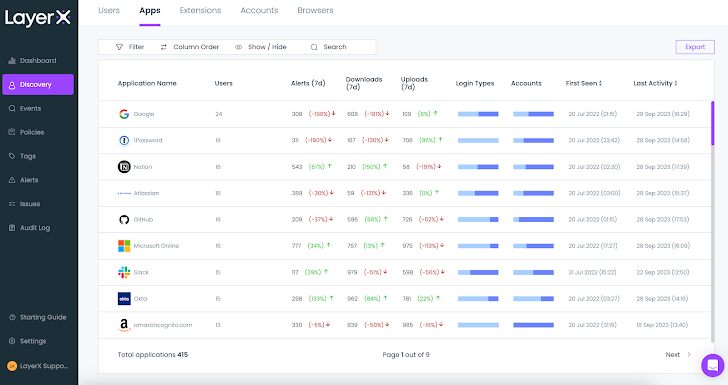 |
| Determine 3: The LayerX Discovery display, Apps part |
Proactively Detecting and Resolving Browser Points
The Discovery course of informs the person about numerous points, enabling the person to resolve them on the spot. For instance, reviewing the completely different extensions would possibly reveal an extension that has essential permissions that might expose it to compromise. In such a case, the extension can merely be added to a block record, eliminating the chance.
Furthermore, LayerX supplies a devoted ‘Points’ tab that aggregates all of the findings that point out a possible safety weak spot for every entity kind. For accounts, it might be weak passwords or shared accounts. For purposes, public app uploads or non-SSO company apps. And so on.
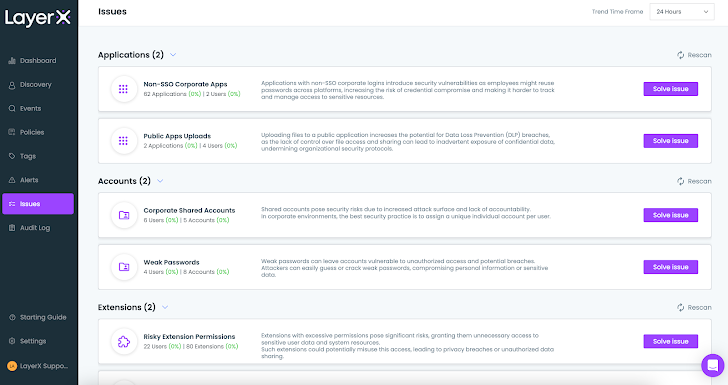 |
| Determine 4: The LayerX Points display displaying Account and Utility points |
It is essential to notice that that is the primary time that a lot of the information displayed within the Discovery web page is offered for monitoring and evaluation. Current IT and safety merchandise weren’t in a position to current it. As such, LayerX addresses an extended acknowledged blind spot.
Detecting and Resolving Malicious Browser Extensions Threat
One of the vital essential and unaddressed dangers are malicious browser extensions. These extensions have the ability to compromise browser information, route staff to malicious net pages, seize session information, and perform many different malicious actions.
The ‘Extensions’ tab within the Discovery web page pinpoints all of the extensions that introduce a danger to the setting.
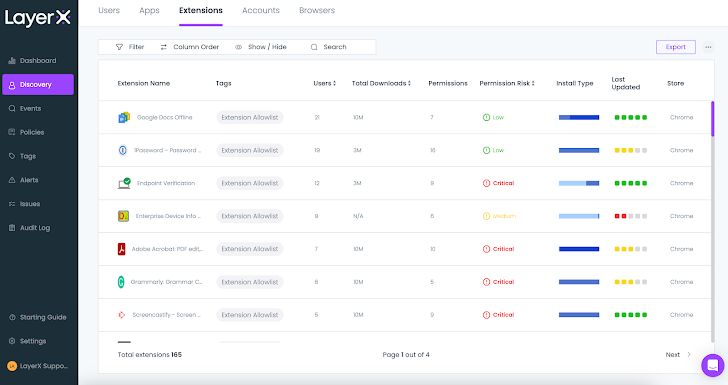 |
| Determine 5: The LayerX Discovery display, Extensions tab |
The ‘Points’ web page aggregates the dangerous extensions and supplies a suggestion on the way to resolve it. This may be carried out manually or with LayerX’s ‘Computerized Resolve’ possibility.
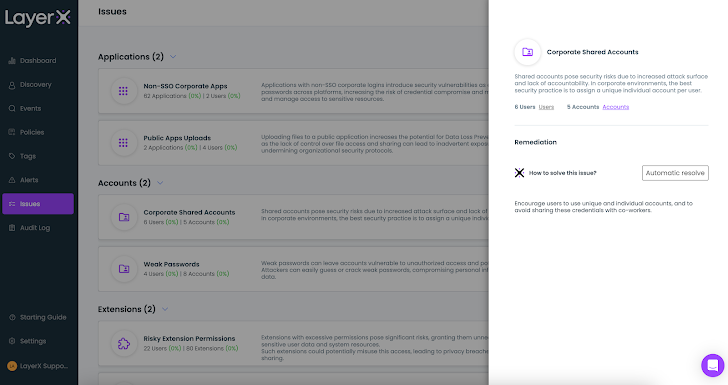 |
| Determine 6: The LayerX Points display displaying handbook and automatic resolving choices |
Following the invention and backbone of present dangerous extensions, the person can proactively mitigate this danger going ahead with a devoted coverage. Earlier than exhibiting how, let’s present perception into LayerX’s coverage configuration function.
LayerX Insurance policies – Easy methods to Clear up Numerous Browser Safety Use Circumstances
LayerX insurance policies allow customers to proactively shield towards a variety of web-borne dangers. Insurance policies are labeled into differing types (DLP, secure looking, and many others.) based mostly on the chance kind they tackle.
The center of the coverage is the ‘Situations’ part, wherein the person determines the situations that set off a protecting motion. These situations can vary from easy guidelines to extraordinarily granular mixtures, enabling laser focus enforcement, decrease false positives and accuracy that can not be achieved by different product
Respectively, the ‘Motion’ half can also be extraordinarily granular, together with each easy ‘block entry’ or ‘forestall add’ actions, in addition to the power to surgically disable dangerous parts throughout the net web page or pop-up warnings to the looking worker.
LayerX is shipped with a set of default insurance policies. Customers can use them as is, modify their situations and actions, or create new ones from scratch.
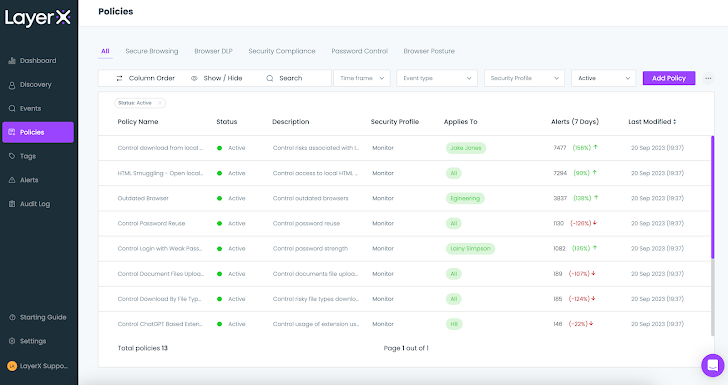 |
| Determine 7: The LayerX Insurance policies display |
Let’s look at a couple of insurance policies as an example this functionality.
A Coverage for Stopping Dangerous Extension Set up
LayerX allows the person to create an inventory of permitted extensions. This record can then be used as a situation parameter to repeatedly monitor and govern this former blind spot.
LayerX supplies its customers with a variety of mitigations towards malicious extensions. Customers can outline a blockallow lists to proactively management which extensions will be put in. As well as LayerX’s granular visibility into the entire extensions’ parts allows customers to configure insurance policies that may block extensions based mostly on their requested permissions, title, set up kind, net retailer and lots of others. this can be a distinctive functionality that can not be present in any endpoint safety or IT administration instrument.
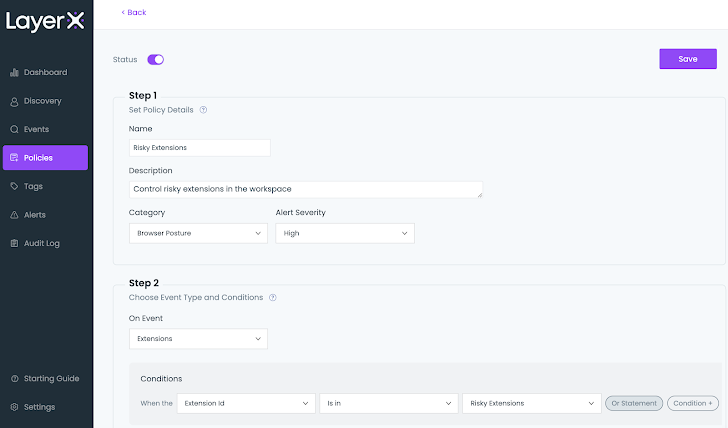 |
| Determine 8: The LayerX Insurance policies display, dangerous extension coverage configuration |
As soon as activated, any try to obtain an extension that is not included within the record will set off a protecting motion. The worker will obtain a pop-up informing them that the extension violates the group’s coverage. Primarily based on the motion configured within the coverage, LayerX will both ask the worker to disable the extension or take motion to robotically deactivate it.
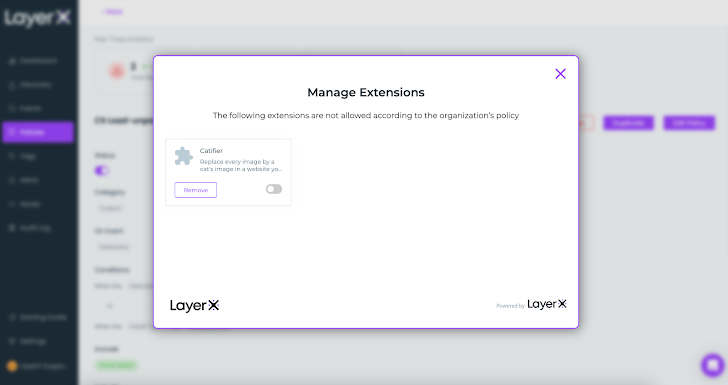 |
| Determine 9: LayerX coverage motion, pop up upon dangerous extension set up |
A Coverage for Stopping Information Leakage by way of ChatGPT
Whereas ChatGPT is a tremendous productiveness booster, it’s crucial to make sure that staff use it in a safe method and with out exposing delicate information.
The coverage under exhibits how this danger will be mitigated. Within the ‘Situations’ part, the person defines the goal website and which kind of textual content triggers a protecting motion. These preliminary situations will be refined by including situations that relate to the system state (managedunmanaged), the browser kind, person identification, and extra.
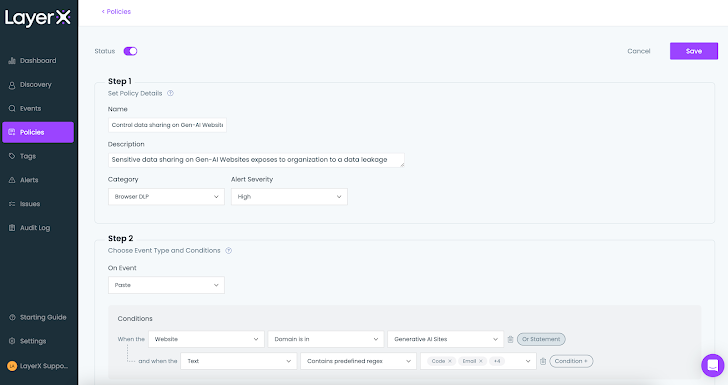 |
| Determine 10: The LayerX coverage display, setting a situation throughout coverage configuration |
A coverage can set off numerous actions based mostly on the person’s wants. The screenshot under exhibits the completely different choices: monitoring, popping up an worker warning message, ‘forestall with bypass’ that allows staff to finish their ChatGPT question pending they will justify it, and the ultimate possibility of full prevention.
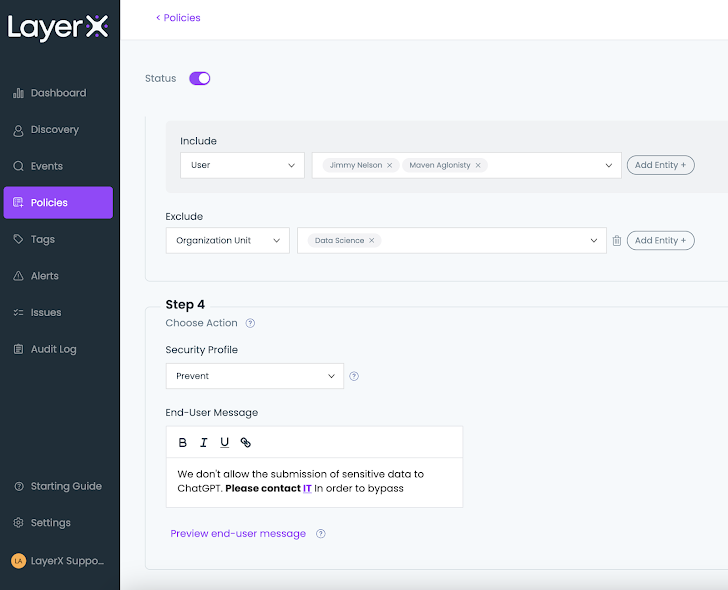 |
| Determine 11: The LayerX coverage display, setting an motion throughout coverage configuration |
As soon as the coverage is configured and enabled, customers can nonetheless use ChatGPT freely, until delicate information is topic to leakage danger. Any violation of the situations outlined within the coverage will set off the configured safety, as effectively an alert that notifies the admin of the violation and its particulars:
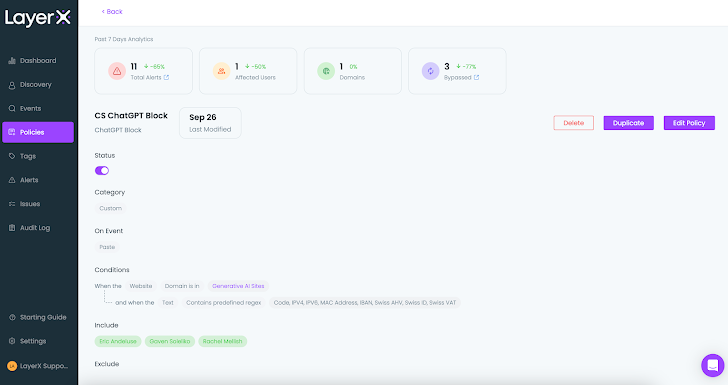 |
| Determine 12: LayerX coverage display, a single coverage web page |
One other essential problem LayerX insurance policies allow resolving is Shadow Identification. This danger surfaces primarily inside sanctioned apps. Suppose the person’s group is utilizing Google Suite, with staff accessing it with a company identification. Nevertheless, in addition they have a private Google account that introduces an information leakage danger if an worker unintentionally uploads recordsdata with delicate information to their private drive or electronic mail slightly than to the company one.
To unravel this problem, LayerX allows customers to configure insurance policies which can be delicate to the worker’s identification and add the identification as a situation, along with file content material, labeling, and different conventional DLP attributes. As soon as enabled, the coverage prevents importing of company information to Google, until it is accessed by the person’s company account.
Hardening Safety In opposition to Account Takeover with LayerX as an Further authentication Issue
LayerX will be built-in with the setting’s cloud Identification Supplier (IdP). In that method, entry to the SaaS apps the IDP manages is feasible solely from a browser on which the extension is put in. For instance, when accessing a SaaS app by way of Okta with out LayerX on the browser, an alert message is triggered:
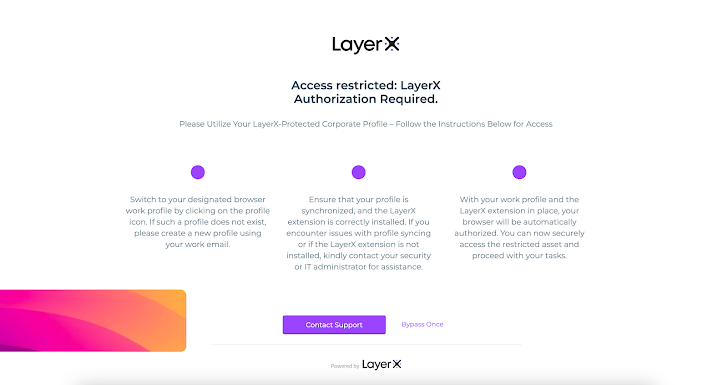 |
| Determine 13: The LayerX entry restriction pop-up |
LayerX serves right here as an MFA, however with out the intrusive person expertise of the push notification to the worker’s cellphone. This serves as extraordinarily efficient mitigation towards malicious entry that exploits compromised credentials, since adversaries won’t ever get entry to SaaS and net assets based mostly on credentials alone.
Monitoring the Net-borne Threats Panorama from the Alerts Display
The ultimate LayerX display on this overview is the Alerts display. Each triggered coverage registers an alert. The Alerts display classifies and aggregates the alert by severity (low, medium, excessive, essential) and kind (paste, secure looking, and many others.), and exhibits the highest triggered insurance policies.
The person can use the varied filters to view solely alerts inside a sure timeframe, kind, motion kind, or danger degree.
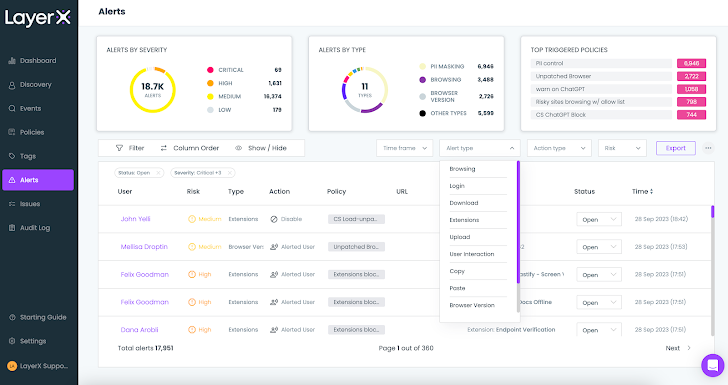 |
| Determine 14: The LayerX entry Alerts display with the Alert Sort dropdown |
For instance, filtering for the ‘Add’ kind will present all of the insurance policies that have been triggered by staff who uploaded recordsdata in an insecure method. Clicking on ‘Examine’ reveals the staff’ looking path and the precise level throughout the session that violated the coverage.
For instance, the next occasion journey for an information add coverage exhibits that the worker uploaded a file to their private Gmail after which switched again to their work account. Detecting and blocking such an occasion is a singular functionality that may’t be carried out by any CASB or different application-oriented safety instrument, since they lack the potential to distinguish between accounts for a similar app.
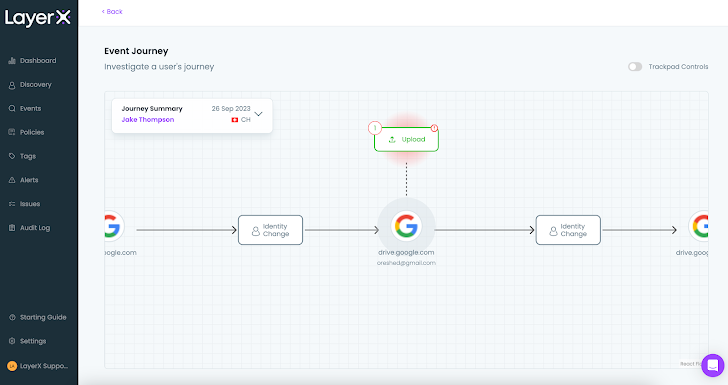 |
| Determine 15: The occasion journey for a triggered DLP coverage |
Conclusion
The LayerX safe browser extension consolidates safety measures for the complete vary of web-borne dangers. A few of these dangers are partially addressed by present options, whereas most have been a whole blind spot, till now.
For organizations that acknowledge the centrality of the browser of their operations, LayerX is a useful answer, offering a single pane of glass for all of the functionalities that mitigate each browser-based assaults and web-related information loss.
[ad_2]