[ad_1]
Cybersecurity researchers have uncovered a brand new set of malicious packages revealed to the NuGet package deal supervisor utilizing a lesser-known methodology for malware deployment.
Software program provide chain safety agency ReversingLabs described the marketing campaign as coordinated and ongoing since August 1, 2023, whereas linking it to a host of rogue NuGet packages that had been noticed delivering a distant entry trojan known as SeroXen RAT.
“The risk actors behind it are tenacious of their want to plant malware into the NuGet repository, and to repeatedly publish new malicious packages,” Karlo Zanki, reverse engineer at ReversingLabs, mentioned in a report shared with The Hacker Information.
The names of a few of the packages are beneath –
- Pathoschild.Stardew.Mod.Construct.Config
- KucoinExchange.Web
- Kraken.Change
- DiscordsRpc
- SolanaWallet
- Monero
- Fashionable.Winform.UI
- MinecraftPocket.Server
- IAmRoot
- ZendeskApi.Shopper.V2
- Betalgo.Open.AI
- Forge.Open.AI
- Pathoschild.Stardew.Mod.BuildConfig
- CData.NetSuite.Web.Framework
- CData.Salesforce.Web.Framework
- CData.Snowflake.API
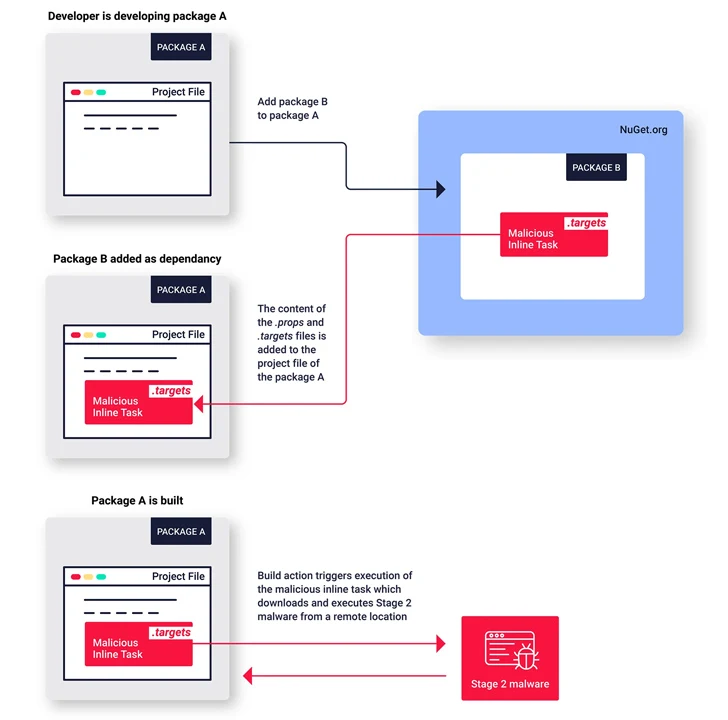
These packages, which span a number of variations, imitate fashionable packages and exploit NuGet’s MSBuild integrations function to be able to implant malicious code on their victims, a function known as inline duties to attain code execution.
“That is the primary identified instance of malware revealed to the NuGet repository exploiting this inline duties function to execute malware,” Zanki mentioned.
The now-removed packages exhibit comparable traits in that the risk actors behind the operation tried to hide the malicious code by making use of areas and tabs to maneuver it out of view of the default display width.
As beforehand disclosed by Phylum, the packages even have artificially inflated downloaded counts to make them seem extra reliable. The last word purpose of the decoy packages is to behave as a conduit for retrieving a second-stage .NET payload hosted on a throwaway GitHub repository.
“The risk actor behind this marketing campaign is being cautious and being attentive to particulars, and is set to maintain this malicious marketing campaign alive and lively,” Zanki mentioned.
[ad_2]