[ad_1]
Microsoft Azure {hardware}’s safety posture is foundational to the safety guarantees we make to our clients. The provision chain of Microsoft Azure servers depends on a multifaceted and sophisticated ecosystem of companions throughout silicon manufacturing, meeting, methods integration, transit, and operationalization in information facilities. A number of interplay factors throughout this provide chain pose vital threats to the safety and integrity of an Azure server touchdown in manufacturing. These dangers embrace firmware tampering, {hardware} tampering, set up of malicious code or spy ware, weakened safety controls, and lots of extra. We at Microsoft consider it’s essential to construct mechanisms to proactively detect and remediate such points in the course of the early phases of product improvement or earlier than servers dock in a knowledge middle.
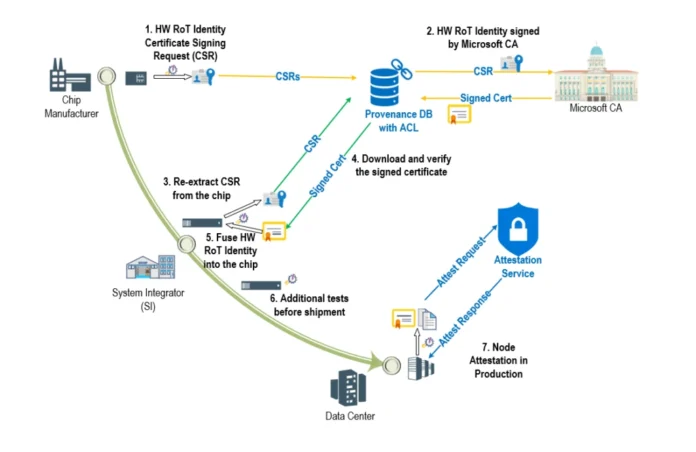
{Hardware} Root-of-Belief (RoT) units resembling Cerberus and Trusted Platform Module are the cornerstone for establishing foundational belief on {hardware} parts in our cloud. This ensures the authenticity and integrity of those parts and their firmware with traceability all the way in which again to silicon manufacturing. The easiest way to perform our goal is to confirm “provenance” of our servers all through their lifecycle from manufacturing unit to manufacturing utilizing {hardware} RoT gadget identities. In the course of the silicon manufacturing course of, the gadget id is securely extracted and annotated to uniquely determine trusted units. This mitigates the chance of “rogue” units discovering their manner into the Azure fleet undetected (Determine 1). Lenovo is considered one of our main provider companions which are pushing the boundaries of safe provide chain with us.
To additional defend these {hardware} RoT identities on which we anchor the chain of belief, we leverage the energy of enclaves and the Confidential Consortium Framework with Microsoft Azure confidential ledger to integrity-protect our provider provenance database. Be taught extra about our firmware integrity protections.
Azure confidential ledger integrity protects present databases and purposes by performing as a point-in-time supply of reality which supplies cryptographic proofs in verification situations. Particularly, saved information isn’t solely immutable and tamper-proof within the append-only ledger however can be independently verifiable. Additionally it is helpful as a repository of audit trails or information that should be saved intact and selectively shared with sure personas. Information logged within the ledger stays immutable, privacy-enhanced, and shielded from insider threats inside a corporation and even the cloud supplier.
On this situation, Azure confidential ledger supplies industry-leading tamper-evidence capabilities to find out if any unauthorized manipulations have occurred with these delicate gadget identities. At completely different deadlines, verification checks are executed towards the Azure confidential ledger to make sure that the information is constant and pristine. Utilizing this know-how additionally mitigates tampering dangers from extremely privileged Azure operators.
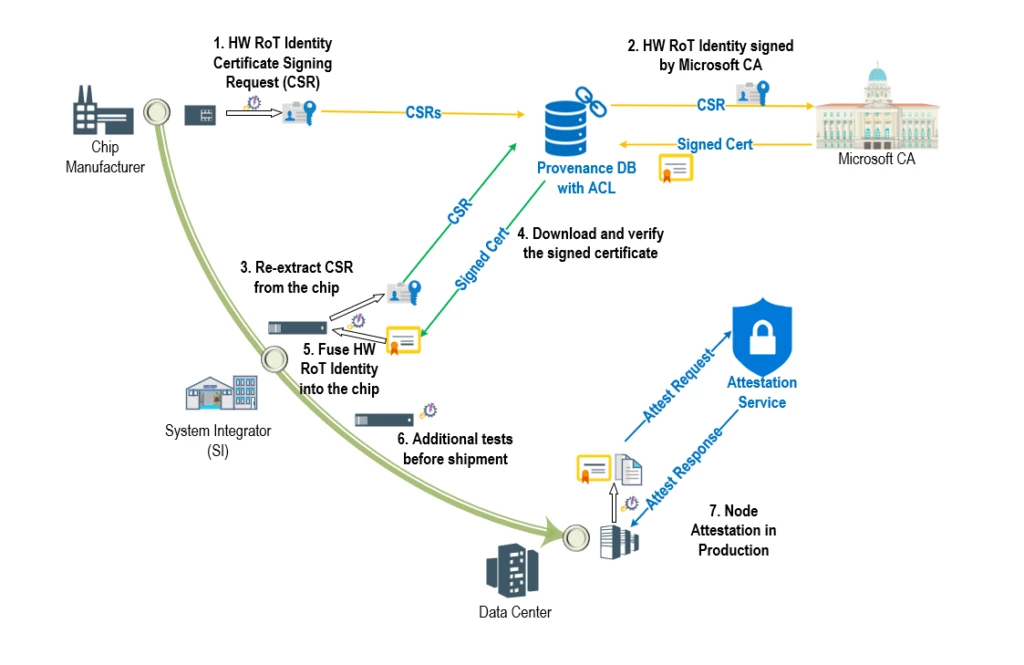
Azure confidential ledger is used to mild up a essential infrastructure safety situation—Challenge Odyssey. Challenge Odyssey goals to cryptographically confirm the provenance of {hardware} RoT units (connected to servers) as they undertake their journey from OEM flooring to Microsoft Azure information facilities and all through their manufacturing lifecycle. As a part of the manufacturing workflow, suppliers add a signed manifest of {hardware} RoT identities right into a trusted ‘provenance database’ that makes use of tamper-evident Azure confidential ledger integration. Because the units are assembled into parts, blades, and racks, their identities may be verified at every step of the availability chain course of. After lengthy journeys by air, land, and sea, the assembled racks arrive at Microsoft Information Facilities the place they endure extra checks to make sure that they weren’t tampered with throughout transit. Lastly, when a server is prepared for manufacturing, it undergoes attestation the place its {hardware} RoT id may be re-verified earlier than permitting it to affix the manufacturing atmosphere and host buyer workloads. Servers are anticipated to endure this course of periodically guaranteeing that the {hardware} parts keep compliant all through their lifecycle, thereby guaranteeing that malicious and unauthorized swapping of blades and motherboards is detected, and non-compliant servers may be tagged for eviction, investigation, and remediation.
This is just one piece of our total {hardware} safety story. Microsoft Azure has developed complete safety necessities to allow safety capabilities resembling safe boot, safe replace, attestation, restoration, encryption, and telemetry to make sure Azure {hardware} is resilient to such assaults by way of sturdy capabilities round prevention, detection, and response.
Learn extra about how we safe Microsoft Azure’s {hardware} and firmware.
At Microsoft, a core a part of our tradition is leveraging the work of one another to ship industry-leading safety to our clients with a protection in-depth strategy. Azure {hardware} gadget provenance and provide chain safety is a basic constructing block of our foundational safety stack. By means of cryptographic provenance verification of Azure {hardware} by way of Challenge Odyssey and extra defense-in-depth protections of {hardware} gadget identities utilizing Azure confidential ledger, we’re setting the gold customary in cloud {hardware} provide chain safety to profit our clients.
“Lenovo’s key precedence is to confirm and make sure the end-to-end safety and traceability for Microsoft cloud {hardware}. By implementing this course of in each our part and system integration factories, not solely can we belief that the {hardware} we obtain from downstream ODM/OEM suppliers is secured and trusted, however we are able to add the Lenovo fingerprint information to the chain of belief, which helps guarantee Microsoft that the {hardware} obtained by information facilities is absolutely secured and reliable.
Integrating this answer into the Lenovo world provide chain workflow was exceptionally easy due to the thorough documentation and examples that the Microsoft group maintains on an ongoing foundation. Assuring the integrity and traceability of information in Azure confidential ledger permits Lenovo to deal with course of and product high quality, without having to spend additional improvement cycles engaged on an in-house safety answer.”—James McFadden, Government Director, Provide Chain High quality & Engineering, Lenovo.
Be taught extra
[ad_2]