
[ad_1]
A proxy botnet known as ‘Socks5Systemz’ has been infecting computer systems worldwide through the ‘PrivateLoader’ and ‘Amadey’ malware loaders, at the moment counting 10,000 contaminated units.
The malware infects computer systems and turns them into traffic-forwarding proxies for malicious, unlawful, or nameless visitors. It sells this service to subscribers who pay between $1 and $140 per day in crypto to entry it.
Socks5Systemz is detailed in a report by BitSight that clarifies that the proxy botnet has been round since a minimum of 2016 however has remained comparatively beneath the radar till lately.
Socks5Systemz
The Socks5Systemz bot is distributed by the PrivateLoader and Amadey malware, which are sometimes unfold through phishing, exploit kits, malvertizing, trojanized executables downloaded from P2P networks, and many others.
The samples seen by BitSight are named ‘previewer.exe,’ and their activity is to inject the proxy bot onto the host’s reminiscence and set up persistence for it through a Home windows service known as ‘ContentDWSvc.’
The proxy bot payload is a 300 KB 32-bit DLL. It makes use of a site era algorithm (DGA) system to attach with its command and management (C2) server and ship profiling information on the contaminated machine.
In response, the C2 can ship one of many following instructions for execution:
- idle: Carry out no motion.
- join: Hook up with a backconnect server.
- disconnect: Disconnect from the backconnect server.
- updips: Replace the record of IP addresses approved to ship visitors.
- upduris: Not carried out but.
The join command is essential, instructing the bot to ascertain a backconnect server connection over port 1074/TCP.
As soon as linked to the risk actors’ infrastructure, the contaminated gadget can now be used as a proxy server and bought to different risk actors.
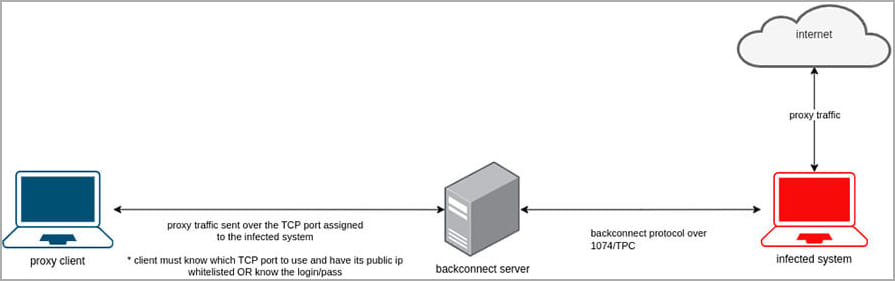
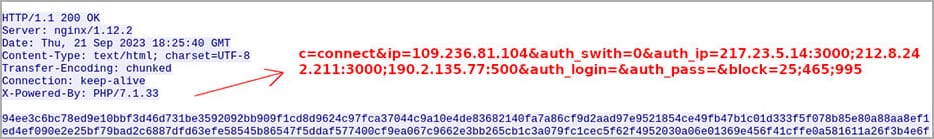
When connecting to the backconnect server, it makes use of fields that decide the IP deal with, proxy password, record of blocked ports, and many others. These subject parameters make sure that solely bots within the allowlist and with the required login credentials can work together with the management servers, blocking unauthorized makes an attempt.
Unlawful enterprise affect
BitSight mapped an in depth management infrastructure of 53 proxy bot, backconnect, DNS, and deal with acquisition servers situated primarily in France and throughout Europe (Netherlands, Sweden, Bulgaria).
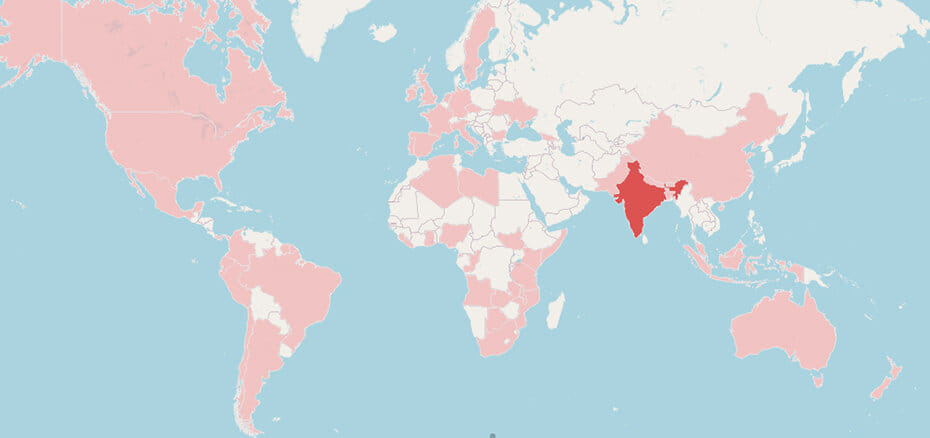
Because the begin of October, the analysts recorded 10,000 distinct communication makes an attempt over port 1074/TCP with the recognized backconnect servers, indicating an equal variety of victims.
The geographic distribution is sparse and random, protecting all the globe, however India, the US, Brazil, Colombia, South Africa, Argentina, and Nigeria rely essentially the most infections.
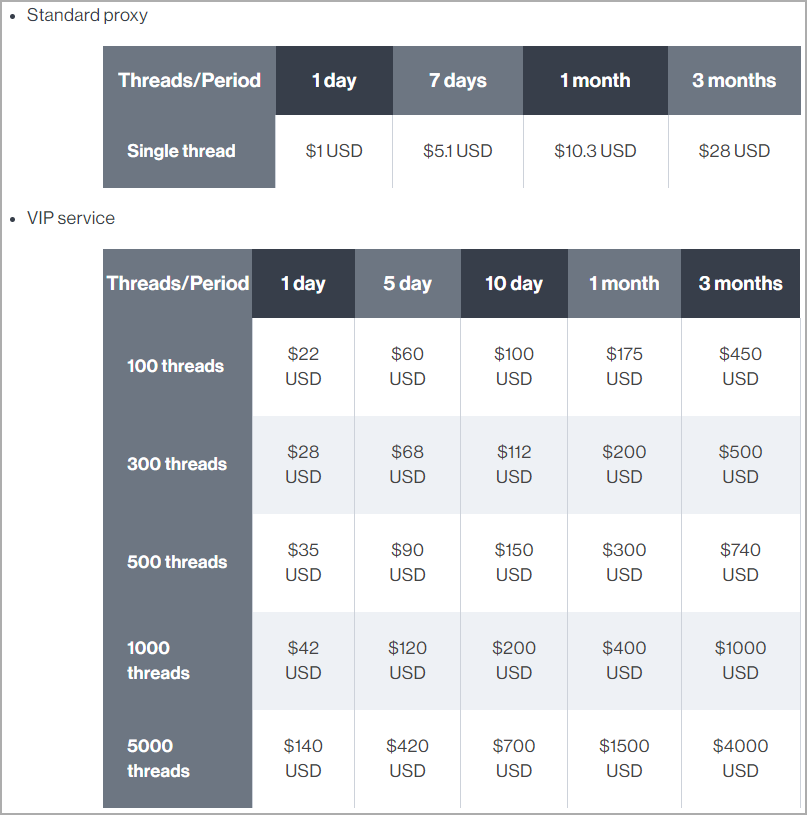
Entry to Socks5Systemz proxying companies is bought in two subscription tiers, particularly ‘Commonplace’ and ‘VIP,’ for which prospects pay through the nameless (no KYC) cost gateway ‘Cryptomus.’
Subscribers should declare the IP deal with from the place the proxied visitors will originate to be added to the bot’s allowlist.
Commonplace subscribers are restricted to a single thread and proxy sort, whereas VIP customers can use 100-5000 threads and set the proxy sort to SOCKS4, SOCKS5, or HTTP.
Costs for every service providing are given under.
Residential proxy botnets are a profitable enterprise that has a big affect on web safety and unauthorized bandwidth hijacking.
These companies are generally used for buying bots and bypassing geo-restrictions, making them very fashionable.
In August, AT&T analysts revealed an in depth proxy community comprising over 400,000 nodes, through which unaware Home windows and macOS customers have been serving as exit nodes channeling the web visitors of others.
[ad_2]