[ad_1]
A complicated pressure of malware masquerading as a cryptocurrency miner has managed to fly the radar for over 5 years, infecting at least a million units world wide within the course of.
That is in response to findings from Kaspersky, which has codenamed the risk StripedFly, describing it as an “intricate modular framework that helps each Linux and Home windows.”
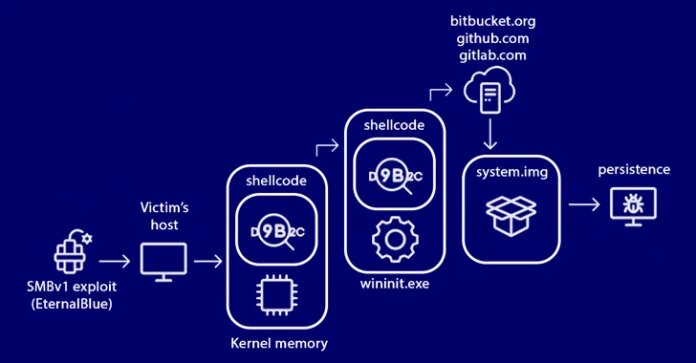
The Russian cybersecurity vendor, which first detected the samples in 2017, mentioned the miner is a part of a a lot bigger entity that employs a customized EternalBlue SMBv1 exploit attributed to the Equation Group with a purpose to infiltrate publicly-accessible methods.
The malicious shellcode, delivered by way of the exploit, has the flexibility to obtain binary information from a distant Bitbucket repository in addition to execute PowerShell scripts. It additionally helps a group of plugin-like expandable options to reap delicate knowledge and even uninstall itself.
The platform’s shellcode is injected within the wininit.exe course of, a legit Home windows course of that is began by the boot supervisor (BOOTMGR) and handles the initialization of numerous providers.
“The malware payload itself is structured as a monolithic binary executable code designed to help pluggable modules to increase or replace its performance,” safety researchers Sergey Belov, Vilen Kamalov, and Sergey Lozhkin mentioned in a technical report revealed final week.
“It comes outfitted with a built-in TOR community tunnel for communication with command servers, together with replace and supply performance via trusted providers corresponding to GitLab, GitHub, and Bitbucket, all utilizing customized encrypted archives.”
Different notable spy modules enable it to collect credentials each two hours, seize screenshots on the sufferer’s system with out detection, document microphone enter, and begin a reverse proxy to execute distant actions.
Upon gaining a profitable foothold, the malware proceeds to disable the SMBv1 protocol on the contaminated host and propagate the malware to different machines utilizing an worming module by way of each SMB and SSH, utilizing keys harvested on the hacked methods.
StripedFly achieves persistence by both modifying the Home windows Registry or by creating activity scheduler entries if the PowerShell interpreter is put in and administrative entry is out there. On Linux, persistence is achieved by way of a systemd person service, autostarted .desktop file, or by modifying /and many others/rc*, profile, bashrc, or inittab information.
Additionally downloaded is a Monero cryptocurrency miner that leverages DNS over HTTPS (DoH) requests to resolve the pool servers, including an additional layer of stealth to the malicious actions. It has been assessed that the miner is used as a decoy to stop safety software program from discovering the complete extent of the malware’s capabilities.
In an effort to reduce the footprint, malware parts that may be offloaded are hosted as encrypted binaries on numerous code repository internet hosting providers corresponding to Bitbucket, GitHub, or GitLab.
As an illustration, the Bitbucket repository operated by the risk actor since June 2018 consists of executable information able to serving the preliminary an infection payload throughout each Home windows and Linux, checking for brand spanking new updates, and in the end updating the malware.
Communication with the command-and-control (C2) server, which is hosted within the TOR community, takes place utilizing a customized, light-weight implementation of a TOR consumer that’s not based mostly on any publicly documented strategies.
“The extent of dedication demonstrated by this performance is outstanding,” the researchers mentioned. “The aim of hiding the C2 server in any respect prices drove the event of a novel and time-consuming venture – the creation of its personal TOR consumer.”
One other placing attribute is that these repositories act as fallback mechanisms for the malware to obtain the replace information when its main supply (i.e., the C2 server) turns into unresponsive.
Kaspersky mentioned it additional uncovered a ransomware household known as ThunderCrypt that shares important supply code overlaps with StripedFly barring the absence of the SMBv1 an infection module. ThunderCrypt is claimed to have been used towards targets in Taiwan in 2017.
The origins of StripedFly stay presently unknown, though the sophistication of the framework and its parallels to EternalBlue exhibit all of the hallmarks of a complicated persistent risk (APT) actor.
It is value stating that whereas the Shadow Brokers’ leak of the EternalBlue exploit befell on April 14, 2017, the earliest recognized model of StripedFly incorporating EternalBlue dates a yr again to April 9, 2016. Because the leak, the EternalBlue exploit has been repurposed by North Korean and Russian hacking outfits to unfold the WannaCry and Petya malware.
That mentioned, there’s additionally proof that Chinese language hacking teams could have had entry to among the Equation Group’s exploits earlier than they have been leaked on-line, as disclosed by Verify Level in February 2021.
The similarities to malware related to the Equation group, Kaspersky mentioned, can also be mirrored within the coding type and practices resembling these seen in STRAITBIZARRE (SBZ), one other cyber espionage platform wielded by the suspected U.S.-linked adversarial collective.
The event comes practically two years after researchers from China’s Pangu Lab detailed a “top-tier” backdoor known as Bvp47 that was allegedly put to make use of by the Equation Group on greater than 287 targets spanning a number of sectors in 45 international locations.
For sure, a vital side of the marketing campaign that continues to be a thriller – aside from to those that engineered the malware – is its actual goal.
“Whereas ThunderCrypt ransomware suggests a business motive for its authors, it raises the query of why they did not go for the possibly extra profitable path as an alternative,” the researchers mentioned.
“It is tough to just accept the notion that such subtle and professionally designed malware would serve such a trivial goal, given all of the proof on the contrary.”
[ad_2]