[ad_1]

Apple’s “Discover My” location community will be abused by malicious actors to stealthily transmit delicate data captured by keyloggers put in in keyboards.
The Discover My community and utility is designed to assist customers find misplaced or misplaced Apple gadgets, together with iPhones, iPads, Macs, Apple Watches, AirPods, and Apple Tags.
The service depends on GPS and Bluetooth information crowd-sourced from tens of millions of Apple gadgets worldwide to seek out gadgets reported as misplaced or stolen, even when these are offline.
Misplaced gadgets ship Bluetooth indicators in a relentless loop detected by close by Apple gadgets, which then anonymously relay their location to the proprietor by way of the Discover My community.
The potential to abuse Discover My to transmit arbitrary information apart from simply machine location was first found by Constructive Safety researchers Fabian Bräunlein and his group over two years in the past, however apparently, Apple addressed this downside.
The analysts have even printed their implementation on GitHub, referred to as ‘Ship My,’ which others can leverage for importing arbitrary information onto Apple’s Discover My community and retrieving it from any internet-enabled machine anyplace on this planet.
Relaying arbitrary information
As first reported on Heise, the researchers created a proof-of-concept {hardware} machine to higher spotlight the chance to the general public.
They built-in a keylogger with an ESP32 Bluetooth transmitter right into a USB keyboard to point out that it is potential to relay passwords and different delicate information typed on the keyboard by way of the Discover My community through Bluetooth.
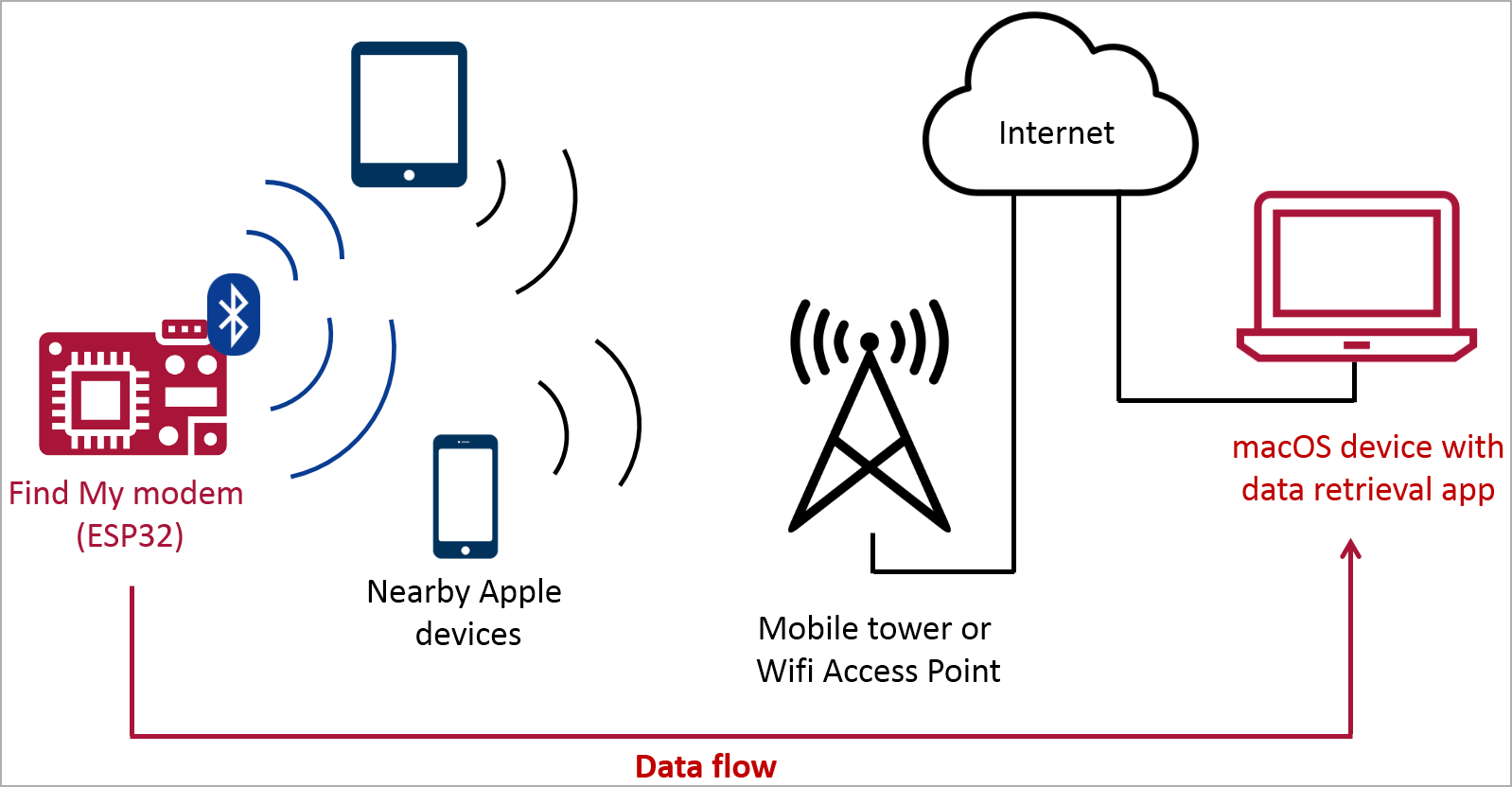
Bluetooth transmission is way stealthier than WLAN keyloggers or Raspberry Pi gadgets that may be simply seen in well-guarded environments, and the Discover My platform can covertly leverage omnipresent Apple gadgets for the relay.
The keylogger would not have to make use of an AirTag or an formally supported chip, as Apple gadgets are tuned to answer any Bluetooth message. If that message is appropriately formatted, the receiving Apple machine will create a location report and add it to the Discover My community.
Supply: Heise
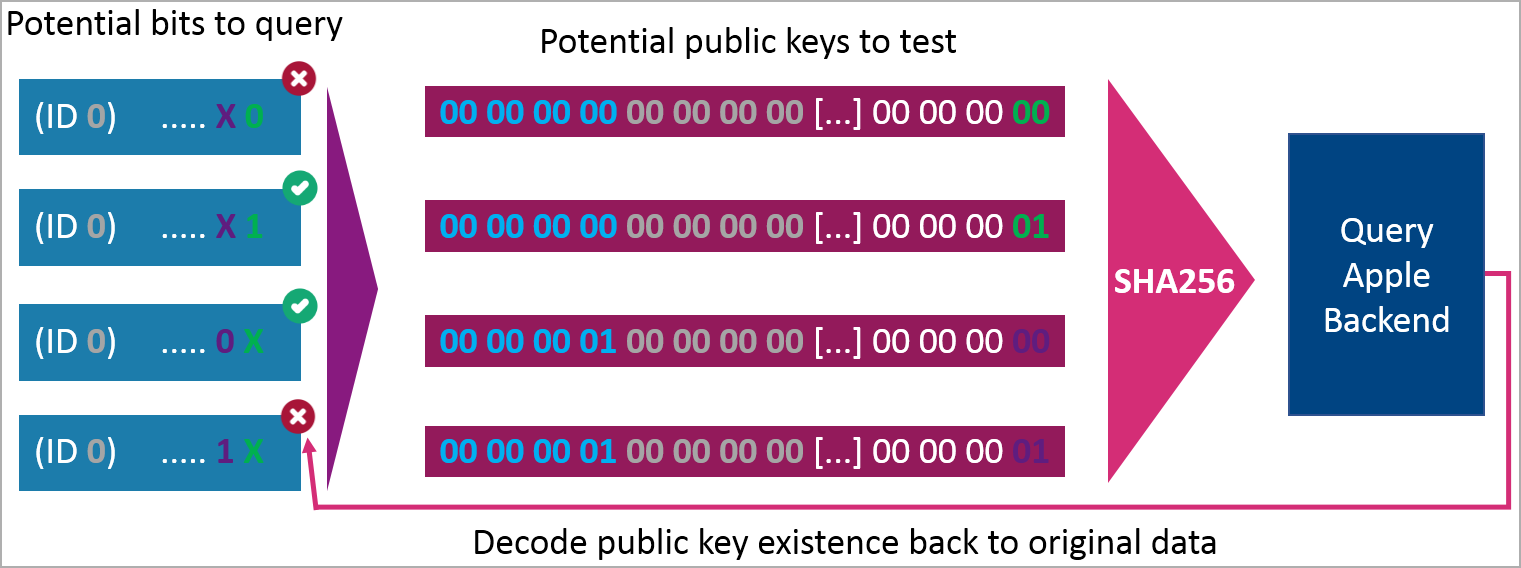
The sender must create many barely completely different public encryption keys simulating a number of AirTags and encode arbitrary information into the keys by assigning particular bits at predetermined positions within the keys.
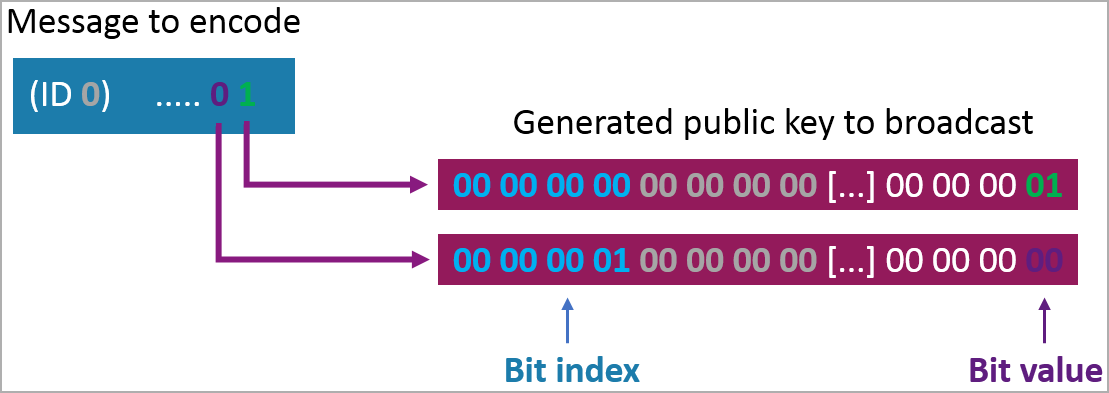
This manner, the a number of experiences retrieved from the cloud will be concatenated and decoded on the receiving finish to retrieve the arbitrary information, on this case, the keylogger’s captures.
Bräunlein defined that the whole value of the data-siphoning contraption was roughly $50, utilizing a Bluetooth-enabled model of the ‘EvilCrow’ keylogger and a typical USB keyboard.

The PoC assault achieved a transmission charge of 26 characters per second and a reception charge of 7 characters/sec, with a latency of between 1 and 60 minutes, relying on the presence of Apple gadgets on the keylogger’s vary.
Whereas that is admittedly not very quick, if recovering useful data comparable to passwords is the aim, ready for a number of hours and even days would not be a deal-breaker for malicious actors.
The very best half is that Apple’s anti-tracking protections that notify customers Air Tags is likely to be monitoring them will not be activated by the stationary keylogger contained in the keyboard, so the machine stays hidden and unlikely to be found.
BleepingComputer has requested Apple for an announcement on the abuse of Discover My, however we have now not obtained a response by publication time.
[ad_2]

